This evening at work I have decided to enable the firewall on my webserver. It is ofcourse already behind my network firewall, but if one of my other devices gets hack or something, it could become a target. I have been meaning to do it for a while now, but it’s probably been tweenty years since I’ve used iptables to do anything. And Ubuntu has a handly little utility called Uncomplicated Firewall(ufw), which is just a configuration system for iptables. And in keeping with linux development over the last couple decades, this new easier configuration comes with all these lovely config files!
Since I’m doing this at work, I have to make sure I’ve got all the rules configured correctly, or I risk being blocked for the rest of the work shift, so gotta dot my t’s and cross my eye’s.
Checking current config
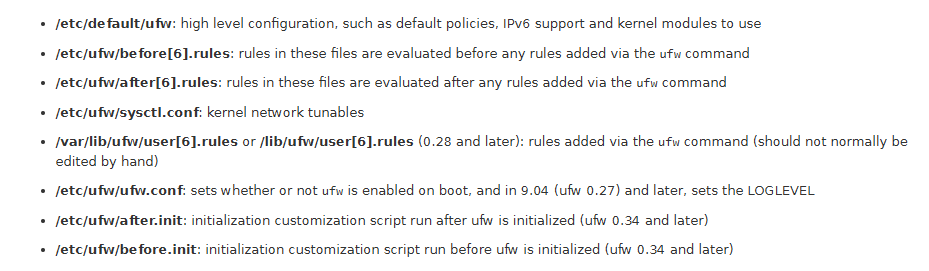
/etc/default/ufw only had a couple things I might need to change, which are listed below.
# Set the default input policy to ACCEPT, DROP, or REJECT. Please note that if
# you change this you will most likely want to adjust your rules.
DEFAULT_INPUT_POLICY="DROP"
# Set the default output policy to ACCEPT, DROP, or REJECT. Please note that if
# you change this you will most likely want to adjust your rules.
DEFAULT_OUTPUT_POLICY="ACCEPT"
# Set the default forward policy to ACCEPT, DROP or REJECT. Please note that
# if you change this you will most likely want to adjust your rules
DEFAULT_FORWARD_POLICY="DROP"
# Set the default application policy to ACCEPT, DROP, REJECT or SKIP. Please
# note that setting this to ACCEPT may be a security risk. See 'man ufw' for
# details
DEFAULT_APPLICATION_POLICY="SKIP"
The .rules files I checked just had some common sense stuff, but I haven’t found a “Drop All” command anywhere in the files. I really need to know if this is configured for default deny or allow, because that changes the order I need to add rules. I’m assuming it’s processed last. I attempted to just enable the firewall but I got a message that it may disconnect my ssh session, so I’ve decided to enter the rules I know I need and hope I don’t get blocked when I enable it.
So, building the commands to add the rules I need, which is HTTP(S) for the webserver, SSH to configure the webserver, and I’ll add some rules for RDP and Samba later, though I’m not sure I really need to because it’s acting as client. Apache and SSH are already defined as applications in /etc/ufw/applications.d.
# add rule for SSH
sudo ufw allow from 192.168.0.0/24 to any app OpenSSH
#add rule for Apache
sudo ufw allow from any to any app "Apache Full"
Unfortunately, it doesn't all me to run the status command without enabling the firewall, so I may have 7-8 hours of boredom if this goes titts up.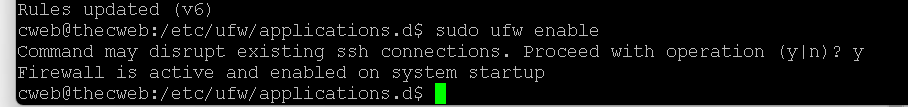
Wow, I wasn’t disconnected, so I did things right, or it’s just not blocking anything at all. Time to check the log.
Nothing but this error, so I think I’m good. Not sure why my router is sending this shit, but I’m guessing it’s UNPNP or Multicast something or other. It logs this every 20 seconds.
2024-10-20T04:25:18.125010+00:00 thecweb kernel: [UFW BLOCK] IN=eno1 OUT= MAC=01:00:5e:00:00:01:c8:7f:54:90:f5:d8:08:00 SRC=192.168.1.1 DST=224.0.0.1 LEN=36 TOS=0x00 PREC=0x00 TTL=1 ID=11284 DF PROTO=2I’m kind of surpised neither my SSH, RDP, or Apache/Tomcat lost connection when I turned it on, but things seem to be working perfectly…

The status command certialy looks like I did what I inteneded…
cweb@thecweb:/var/log$ sudo ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
80/tcp ALLOW IN Anywhere
443/tcp ALLOW IN Anywhere
22/tcp (OpenSSH) ALLOW IN 192.168.0.0/24
80,443/tcp (Apache Full) ALLOW IN Anywhere
80/tcp (v6) ALLOW IN Anywhere (v6)
443/tcp (v6) ALLOW IN Anywhere (v6)
80,443/tcp (Apache Full (v6)) ALLOW IN Anywhere (v6)One last setting to enable at boot and I’m done. Oh, well actually, it turns out that /etc/ufw/ufw.conf is automatically updated to start on boot with the ufw enable command. Cool.